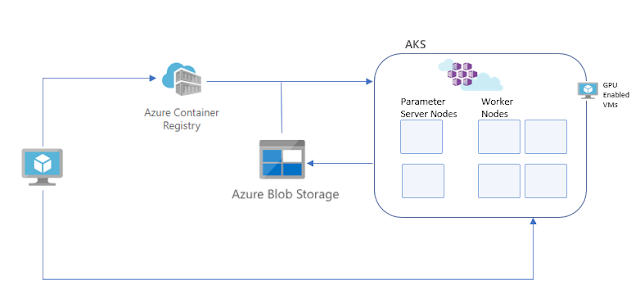
For brick and mortar retailers, the world has been overturned. Online retailers have been demolishing their market share and icons of commerce are struggling. But what helped online retailers can help the offline. The cloud can also be used by brick and mortar retailers. In fact, the brick and mortar experience, transformed with cloud technology, can be a real advantage in competition with online only.
Cloud technologies are enabling new capabilities and those new powers are disrupting the business models of traditional retailers and sellers of consumer goods. The cloud is at the heart of digital transformation.
◈ It is changing the way technology is implemented and managed.
◈ It offers the benefit of massive scale, increased business speed, and organizational agility.
◈ It makes possible economic benefits related to variable expense, maintenance and deployment.
◈ It enables seamless consumer experiences between offline and online.
◈ It encourages differentiated experiences that wow customers.
Now you have the key to competing in today’s landscape. For these reasons, it is no longer a question of “if,” but “when” and “how” to move to the cloud for most brands.
Reasons for retailers and consumer brands to move to the cloud
Cloud technologies are enabling new capabilities and those new powers are disrupting the business models of traditional retailers and sellers of consumer goods. The cloud is at the heart of digital transformation.
◈ It is changing the way technology is implemented and managed.
◈ It offers the benefit of massive scale, increased business speed, and organizational agility.
◈ It makes possible economic benefits related to variable expense, maintenance and deployment.
◈ It enables seamless consumer experiences between offline and online.
◈ It encourages differentiated experiences that wow customers.
Now you have the key to competing in today’s landscape. For these reasons, it is no longer a question of “if,” but “when” and “how” to move to the cloud for most brands.
Business value of the cloud
Born-in-the-cloud retailers are entering the marketplace by solving long-standing consumer challenges in new and innovative ways. Modern technology capabilities allow them to accelerate benefits to both the consumer and business objectives. These new experiences raise the bar on what’s possible. They elevate consumers’ expectations by delivering relevancy and convenience, often at a fraction of the ecosystem footprint of long-standing retailers.
Each organization’s journey to the cloud will be unique. There will be a variety of reasons and benefits that should be acknowledged. However, here are the four major categories for cloud business value: cost, agility, performance, and new sources of value.
Evolved cost structure and transparency
Innovation doesn’t stop because of an organization’s budgeting cycle. Your internal processes should not impact your speed and agility to deliver improved experiences to your consumers. If it does, as a leader you should add those processes to your list of things to evolve.
The cloud enables and encourages a continuous planning approach. It allows you to reap the full benefits of the cloud despite the traditional annual budgeting cycles. The dominant conversation related to cost becomes the shift from CapEx to OpEx. This fundamentally changes how organizations budget and pay for technology. Since fixed costs associated with shared infrastructure are distributed, the cloud enables greater visibility into the true cost of individual applications. The shift to variable expense offers the organization the ability to begin executing more quickly. And the organization becomes more agile through a fail-fast approach, especially given the lower barrier to initiatives. This enables you to experiment and deliver new concepts to customers. And for some brands, the ability to continually test and learn before committing to significant investments is extremely valuable. Especially when determining the relevancy of the offer and viability of the concept.
Improved agility, speed and productivity
Developing and deploying via on-premises infrastructures (datacenters) can take weeks to months. The cloud provides greater agility and speed-to-consumer. Development teams can be more productive and can quickly develop services that reach global markets. Azure offers near-instant provisioning, allowing projects to move quickly without the need to over-provision resources. As an added bonus, infrastructure planning costs disappear.
The flexibility of the cloud enables organizations to deploy new approaches more effectively. It lets you deliver value to customers and productivity to the organization. Profits accrue with the adoption of agile software development methodologies, DevOps, CI/CD, and modern SOA and PaaS-based architectures.
Azure cloud, made to order
Azure is designed with the developer in mind. Applications can be built with the language of choice, including Node.js, Java, and .NET. Development tools are available for PC or MAC. Visual Studio and Visual Studio Code are premier environments with built-in features for Azure. For example, mobile app development is accelerated by integrating the development lifecycle with Visual Studio App Center. Features include automated builds, and testing for cross-platform, hybrid, and native apps on iOS and Android.
Most compliant
Azure’s infrastructure has been developed to support global demand. Azure is available in 54 global Azure regions, more than any cloud provider. Azure has 70+ compliance offerings—the largest portfolio in the industry. Azure meets a broad set of international and industry-specific compliance standards, such as General Data Protection Regulation (GDPR), as well as country-specific standards, including Australia IRAP, UK G-Cloud, and Singapore MTCS.
Security matters
Security is essential to you and your customers. Here is a short list of how Azure offers improvements in reliability and security over on-premises infrastructure.
◈ The Azure Security Center spans on-premises and cloud workloads. From a single dashboard, you can monitor and manage all of your resources.
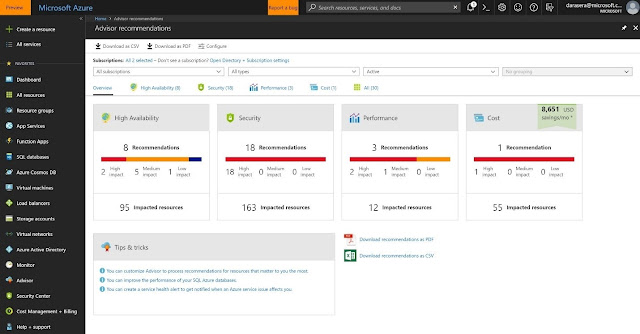
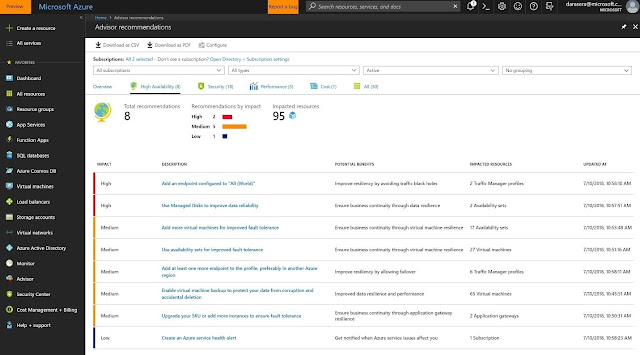
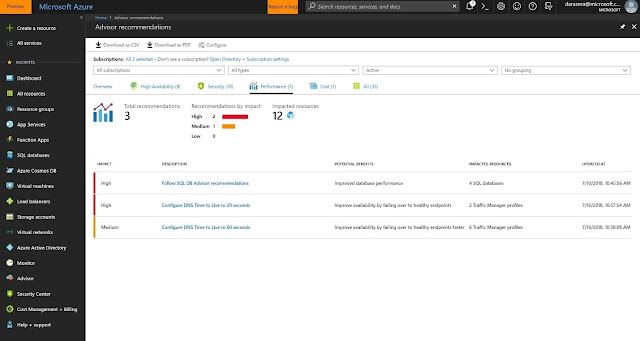
◈ The Azure Advisor is a free service that gives you the best advice based on the most current data. Azure Active Directory helps you to manage user identities and create intelligence-driven access policies to secure your resources.
◈ Site Recovery gives you some assurance that you can recover from a disaster.
◈ Individual services have security features. For example, see the security features of Azure SQL Database.
Possibilities to wow customers
The cloud enables unlimited computing scale and storage while removing boundaries. This freedom is a distinct advantage over on-premises infrastructure. This opens a wealth of new opportunities. It frees your organization’s creatives. They can imagine, prototype, and deliver new experiences that wow customers, leading to new business model opportunities.
These cloud capabilities, plus the availability of data and digital networks, provide an opportunity for modern technologies such as artificial intelligence, IoT, machine learning, and AR/VR to thrive. These technologies enable you to innovate and experiment. This leads to competitive advantages, many of which are only available in the cloud, and that are cost-prohibitive if implemented on-premises.
This is where it gets exciting for retail and consumer goods brands who are focused on delivering new and/or improved digital experiences. The cloud opens possibilities as new data signals are captured and used to provide insights fuelled with artificial intelligence.