In our 2020 retrospective, we highlighted shifts in the active cyberthreat landscape. With the huge surge in internet activity, particularly with the onset of the COVID-19 pandemic, Distributed Denial-of-Service (DDoS) attacks have ramped up significantly in both volume and complexity.
We continue to see such trends in the first half of the calendar year 2021. With the increased usage and supply of IoT devices as well as cryptocurrency like Bitcoin (which is hard to trace), we see a rise in ransomware and ransom DDoS attacks1, whose victims included Mexico’s national lottery sites2 as well as Bitcoin.org3, among others. The online gaming vertical continues to be a very attractive target of DDoS attacks, as experienced by Respawn Entertainment throughout the past few months who suffered significant disruptions to Titanfall’s gameplay4. More industries are being targeted, particularly higher education5, healthcare6, telecoms7, and public sectors. In May, a DDoS attack on Belnet, the internet service provider (ISP) for Belgium’s public sector, took down the websites of more than 200 organizations8 that included the Belgian government, parliament, universities, and research institutes.
Read More: AZ-900: Microsoft Azure Fundamentals
At Microsoft, the Azure DDoS Protection team protects every property in Microsoft and the entire Azure infrastructure. In this review, we share trends and insights into DDoS attacks we observed and mitigated throughout the first half of 2021.
Number of attacks
During the first half of 2021, we witnessed a sharp increase in DDoS attacks per day. Compared to Q4 of 2020, the average daily number of attack mitigations in the first half of 2021 increased by 25 percent. We mitigated an average of 1,392 attacks per day, the maximum reaching 2,043 attacks on May 24, 2021. In total, we mitigated upwards of 251,944 unique attacks against our global infrastructure during the first half of 2021.
Attack bandwidth
In the first half of 2021, the largest attack bandwidth reported on Azure resources was 625 Gbps, down from 1 Tbps in Q3 of 2020. However, the average attack size increased by 30 percent, from 250 Gbps to 325 Gbps.
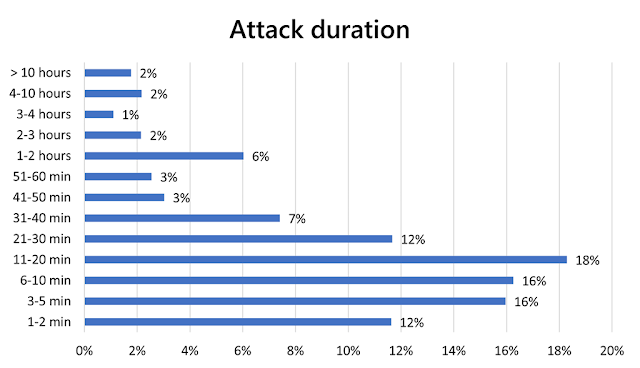
Attack duration
As with 2020, we continue to see that most attacks are short-lived, with 74 percent being 30 minutes or less and 87 percent being one hour or less.
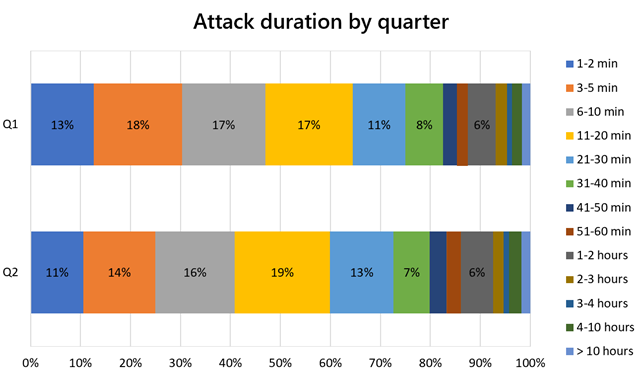
The proportion of short-lived attacks remained largely consistent across the first half of 2021. Seventy-six percent of attacks in Q1 of 2021 were 30 minutes or less duration, compared to 73 percent of attacks in Q2.
This year, we see more advanced techniques being employed by attackers, such as recycling IPs to launch short-burst attacks.
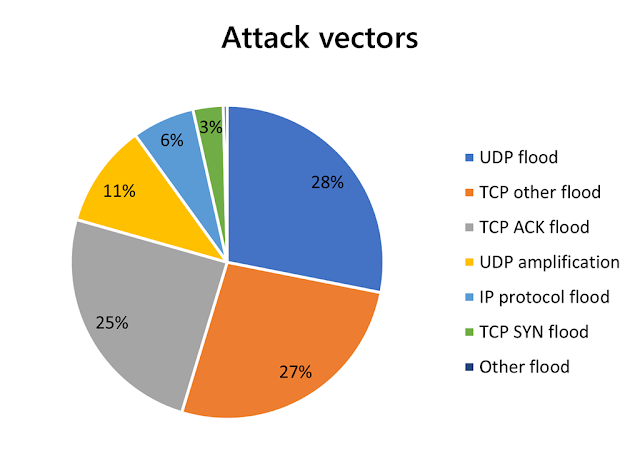
Top attack vectors
Compared to 2020, we see a rise in volumetric transmission control protocol (TCP) flood attacks. The first half of 2021 was characterized by a shift towards attacks against web applications, whereby TCP attacks are at 54 percent of all attack vectors (mainly TCP, SYN, SYN-ACK, and ACK floods).
User datagram protocol (UDP) attacks were the top vector in 2020 comprising more than 65 percent of all attacks. In the first half of 2021, they decreased to 39 percent of overall attack vectors, with amplification attacks accounting for 11 percent of total attacks.
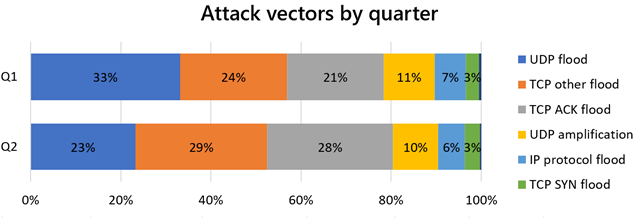
While UDP attacks comprised the majority of attack vectors in Q1 of 2021, TCP overtook UDP as the top vector in Q2. From Q1 to Q2, the proportion of UDP dropped from 44 percent to 33 percent, while the proportion of TCP increased from 48 percent to 60 percent.
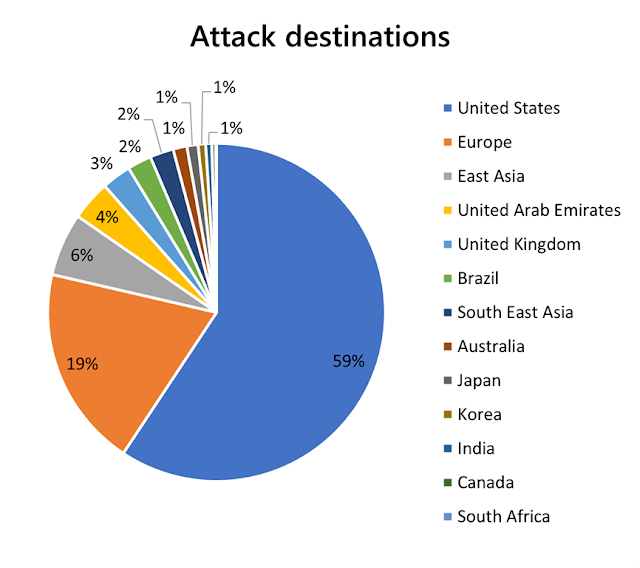
Top attacked regions
Similar to 2020, the United States (59 percent), Europe (19 percent), and East Asia (6 percent) were the most attacked regions due to the concentration of financial services and gaming industries in these regions. As financial institutions tend to rely on TCP workloads, it makes sense that these regions have been harder hit in the first half of 2021, given the rise in TCP flood attacks.
The United Arab Emirates has been increasingly hit by DDoS attacks on government, private, oil and gas, telecommunications, and healthcare sectors. The region was particularly hit hard in January, with 70 percent of its total attacks concentrated in that month.
As with 2020, East Asia (Hong Kong) remains a popular target of DDoS attacks, with 41 percent of its total attacks occurring in May and June. In June, we saw a huge uptick in SYN, SYN-ACK, and ACK flood attacks in the region and we mitigated multiple VIPs totaling up to 225M PPS of traffic.
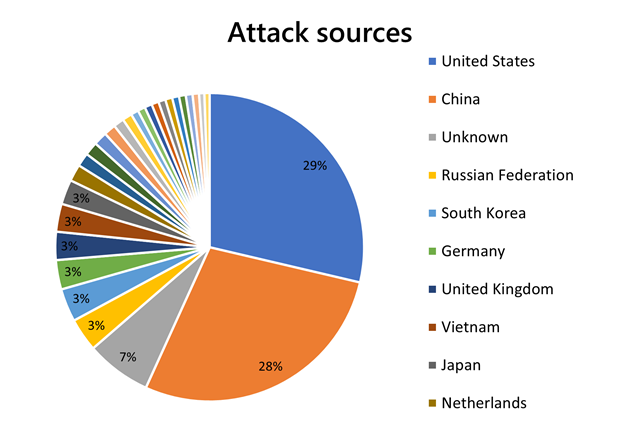
Top attack sources
The top source countries to generate DDoS attacks were the United States (29 percent), China (28 percent), Russia (3 percent), and followed by South Korea (3 percent). Unknown sources (7 percent) indicate that the autonomous system numbers (ASNs) were either garbage, spoofed, or private ASNs that we could not translate.
New attack types observed
New zero-day attack vectors that we observed and defended against:
Microsoft Windows RDP abuse on UDP 3389
In January, Microsoft Windows servers with Remote Desktop Protocol (RDP) enabled on UDP/3389 were being abused to launch UDP amplification attacks. These attacks had an amplification ratio of 85.9:1 and a peak at ~750 Gbps.
D/TLS exploit reflection attack
In February, we saw instances of the Datagram Transport Layer Security (D/TLS) attack vector. Video streaming and gaming customers were getting hit by D/TLS refection attacks which exploited UDP source port 443.
Plex Media server abuse
In June, we saw an emerging reflection attack iteration for the Simple Service Delivery Protocol (SSDP). This protocol normally uses source port 1900, and the new mutation was either on source port 32414 or 32410, also known as Plex Media Simple Service Delivery Protocol (PMSSDP).
Protect your workloads with Azure DDoS Protection Standard
The world continues to be heavily dependent on digital services. We see a growing reliance on cloud-computing services, across sectors from financial services to healthcare. Cyberthreats are pervasive and ever-evolving, and it is always crucial for businesses to develop a robust
DDoS response strategy and be proactive in protecting their public workloads.
Azure DDoS Protection Standard provides enhanced DDoS mitigation features to defend against DDoS attacks. It is automatically tuned to protect all public IP addresses in virtual networks. Protection is
simple to enable on any new or existing virtual network and does not require any application or resource changes. Our recently released
Azure built-in policies allow for better management of network security compliance by providing great ease of onboarding across all your virtual network resources and configuration of logs.
With the recent rise of web application DDoS attacks, it is best to use DDoS Protection Standard alongside Application Gateway web application firewall (WAF), or a third-party web application firewall deployed in a virtual network with a public IP, for comprehensive protection. This also works if you are using Azure Front Door alongside Application Gateway, or if your
backend resources are in your on-premises environment. Additionally, when Application Gateway with WAF is deployed in a DDoS protected virtual network, there are no additional charges for WAF—you pay for the Application Gateway at the
lower non-WAF rate.
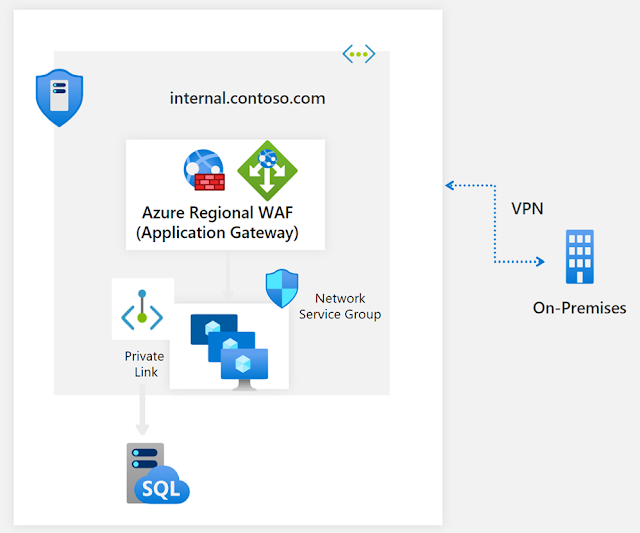
If you have a web application that receives traffic from the Internet and is deployed regionally, you can host your application behind Application Gateway, then protect it with a WAF against Layer 7 web attacks and enable DDoS Protection Standard on the virtual network which contains the Application Gateway and WAF. The backend origins of your application will be in your on-premises environment, which is connected over the virtual private network (VPN). DDoS Protection Standard will defend your application by mitigating bad traffic and routing the supposed clean traffic to your application.
Azure DDoS Protection Standard offers the following key benefits:
◉ Backed by the Microsoft global network: We bring massive DDoS mitigation capacity to every Azure region, scrubbing traffic at the Azure network edge before it can impact the availability of your services. If we identify that the attack volume is significant, we leverage the global scale of Azure to defend the attack from where it is originating.
◉ Cost protection: DDoS attacks often trigger the automatic scale-out of the service running in Azure. This could lead to a significant increase in network bandwidth, the scaling-up of the virtual machine count, or both. In the event of an attack, you can receive Azure credits for any scale-out of resources, so you do not have to worry about setting your application to auto-scale or paying the excess cost for egress data transfer.
◉ DDoS Rapid Response: During an active attack or after an attack, you can engage the DDoS Protection Rapid Response team for help with attack investigation and specialized support. The DDoS Protection Rapid Response team follows the
Azure Rapid Response support model.
◉ Rich attack analytics: With DDoS attack analytics, you can view metrics, configure alerts, and get detailed mitigation reports and flow logs that give you detailed visibility into attack traffic and actions we are taking to mitigate a DDoS attack. You can also
connect your logs to Azure Sentinel, and view and analyze your data in workbooks. With Azure Security Center, we offer alerts whenever your public IP is under a DDoS attack, or if the attack has been mitigated by us, and we also offer recommendations to enable DDoS Standard for your unprotected virtual networks.
Source: microsoft.com








0 comments:
Post a Comment