Why use Security Center?
◈ Continuous security assessment – Monitor the security of machines, networks, storage and data services, and applications to discover potential security issues.
◈ Actionable recommendations – Remediate security vulnerabilities before they can be exploited by attackers with prioritized and actionable security recommendations.
◈ Advanced cloud defenses – Reduce threats with just in time access to management ports and whitelisting to control applications running on your VMs.
◈ Prioritized alerts and incidents - Focus on the most critical threats first with prioritized security alerts and incidents.
◈ Integrated security solutions - Collect, search, and analyze security data from a variety of sources, including connected partner solutions.
The Security Center - Overview provides a quick view into the security posture of your Azure and non-Azure workloads, enabling you to discover and assess the security of your workloads and to identify and mitigate risk. The built-in dashboard provides instant insights into security alerts and vulnerabilities that require attention.
Centralized policy management
A security policy defines the desired configuration of your workloads and helps ensure compliance with company or regulatory security requirements. In Security Center, you define policies and tailor them to your type of workload or the sensitivity of your data.
Security Center policies contain the following components:
◈ Data collection: Determines agent provisioning and security data collection settings.
◈ Security policy: Determine which controls Security Center monitors and recommends by editing the security policy.
◈ Email notifications: Determines security contacts and e-mail notification settings.
◈ Pricing tier: Defines Free or Standard pricing selection. The tier you choose determines which Security Center features are available for resources in scope.
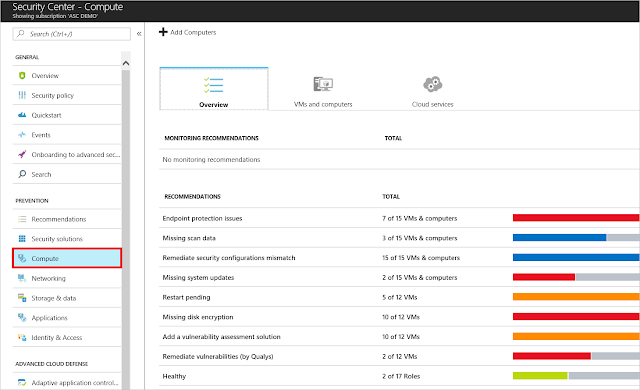
Continuous security assessment
Security Center analyzes the security state of your compute resources, virtual networks, storage and data services, and applications. Continuous assessment helps you to discover potential security issues, such as systems with missing security updates or exposed network ports. Select a tile in the Prevention section to view more information, including a list of resources and any vulnerabilities that have been identified.
Actionable recommendations
Security Center analyzes the security state of your Azure and non-Azure resources to identify potential security vulnerabilities. A list of prioritized security recommendations guides you through the process of addressing security issues.
Just in time VM access
Reduce the network attack surface with just in time, controlled access to management ports on Azure VMs, drastically reducing exposure to brute force and other network attacks.
Specify rules for how users can connect to virtual machines. When needed, access can be requested from Security Center or via PowerShell. As long as the request complies with the rules, access is automatically granted for the requested time.
Adaptive application controls
Block malware and other unwanted applications by applying whitelisting recommendations adapted to your specific Azure workloads and powered by machine learning.
Review and click to apply the recommended application whitelisting rules generated by Security Center or edit rules already configured.
Prioritized alerts and incidents
Security Center uses advanced analytics and global threat intelligence to detect incoming attacks and post-breach activity. Alerts are prioritized and grouped into incidents, helping you focus on the most critical threats first. You can create your own custom security alerts as well.
You can quickly assess the scope and impact of an attack with a visual, interactive investigation experience, and use predefined or ad hoc queries for deeper exploration of security data.
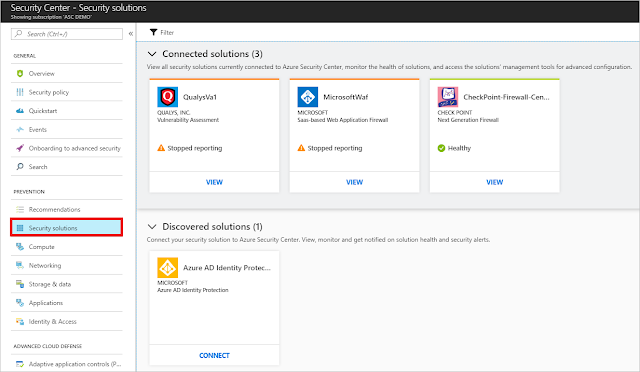
Integrate your security solutions
You can collect, search, and analyze security data from a variety of sources, including connected partner solutions like network firewalls and other Microsoft services, in Security Center.










0 comments:
Post a Comment