Security can be a never-ending saga—a chronicle of increasingly sophisticated attacks, volumes of alerts, and long resolution timeframes where today’s Security Information and Event Management (SIEM) products can’t keep pace.
SecOps teams are inundated with a very high volume of alerts and spend far too much time in tasks like infrastructure set up and maintenance. As a result, many legitimate threats go unnoticed. An expected shortfall of 3.5M security professionals by 2021 will further increase the challenges for security operations teams. You need a solution that empowers your existing SecOps team to see the threats clearer and eliminate the distractions.
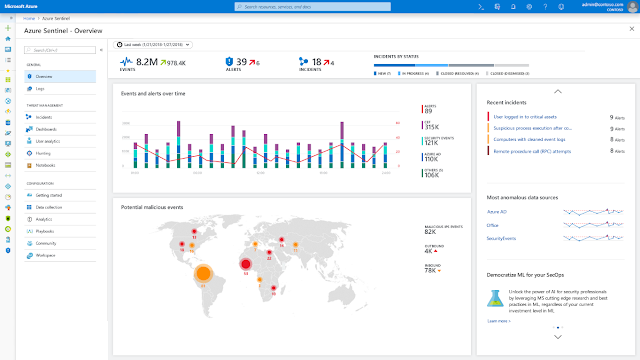
That’s why we reimagined the SIEM tool as a new cloud-native solution called Microsoft Azure Sentinel. Azure Sentinel provides intelligent security analytics at cloud scale for your entire enterprise. Azure Sentinel makes it easy to collect security data across your entire hybrid organization from devices, to users, to apps, to servers on any cloud. It uses the power of artificial intelligence to ensure you are identifying real threats quickly and unleashes you from the burden of traditional SIEMs by eliminating the need to spend time on setting up, maintaining, and scaling infrastructure. Since it is built on Azure, it offers nearly limitless cloud scale and speed to address your security needs. Traditional SIEMs have also proven to be expensive to own and operate, often requiring you to commit upfront and incur high cost for infrastructure maintenance and data ingestion. With Azure Sentinel there are no upfront costs, you pay for what you use.
Many enterprises are using Office 365 and are increasingly adopting the advanced security and compliance offerings included in Microsoft 365. There are many cases when you want to combine security data from users and end point applications with information from your infrastructure environment and third-party data to understand a complete attack.
It would be ideal if you could do this all within the compliance boundaries of a single cloud provider. Today we are announcing that you can bring your Office 365 activity data to Azure Sentinel for free. It takes just a few clicks and you retain the data within the Microsoft cloud.
“With Microsoft Azure Sentinel, we can better address the main SIEM landscape challenges for our clients, along with simplifying data residency and GDPR concerns.”.
SecOps teams are inundated with a very high volume of alerts and spend far too much time in tasks like infrastructure set up and maintenance. As a result, many legitimate threats go unnoticed. An expected shortfall of 3.5M security professionals by 2021 will further increase the challenges for security operations teams. You need a solution that empowers your existing SecOps team to see the threats clearer and eliminate the distractions.
That’s why we reimagined the SIEM tool as a new cloud-native solution called Microsoft Azure Sentinel. Azure Sentinel provides intelligent security analytics at cloud scale for your entire enterprise. Azure Sentinel makes it easy to collect security data across your entire hybrid organization from devices, to users, to apps, to servers on any cloud. It uses the power of artificial intelligence to ensure you are identifying real threats quickly and unleashes you from the burden of traditional SIEMs by eliminating the need to spend time on setting up, maintaining, and scaling infrastructure. Since it is built on Azure, it offers nearly limitless cloud scale and speed to address your security needs. Traditional SIEMs have also proven to be expensive to own and operate, often requiring you to commit upfront and incur high cost for infrastructure maintenance and data ingestion. With Azure Sentinel there are no upfront costs, you pay for what you use.
Many enterprises are using Office 365 and are increasingly adopting the advanced security and compliance offerings included in Microsoft 365. There are many cases when you want to combine security data from users and end point applications with information from your infrastructure environment and third-party data to understand a complete attack.
It would be ideal if you could do this all within the compliance boundaries of a single cloud provider. Today we are announcing that you can bring your Office 365 activity data to Azure Sentinel for free. It takes just a few clicks and you retain the data within the Microsoft cloud.
“With Microsoft Azure Sentinel, we can better address the main SIEM landscape challenges for our clients, along with simplifying data residency and GDPR concerns.”.
Let’s look at how Azure Sentinel will help you deliver cloud-native security operations:
Collect data across your enterprise easily – With Azure Sentinel you can aggregate all security data with built-in connectors, native integration of Microsoft signals, and support for industry standard log formats like common event format and syslog. In just a few clicks you can import your Microsoft Office 365 data for free and combine it with other security data for analysis. Azure Sentinel uses Azure Monitor which is built on a proven and scalable log analytics database that ingests more than 10 petabytes every day and provides a very fast query engine that can sort through millions of records in seconds.
We continue to collaborate with many partners in the Microsoft Intelligent Security Association. Azure Sentinel connects to popular solutions including Palo Alto Networks, F5, Symantec, Fortinet, and Check Point with many more to come. Azure Sentinel also integrates with Microsoft Graph Security API, enabling you to import your own threat intelligence feeds and customizing threat detection and alert rules. There are custom dashboards that give you a view optimized for your specific use-case.
Adam Geller, Senior Vice President, SaaS, virtualization, and cloud-delivered security of Palo Alto Networks said, “We’re pleased with our ongoing collaboration with Microsoft and the work we’re doing to deliver greater security orchestration for our joint customers. This latest integration allows customers to forward their physical and virtualized next generation firewall logs to Azure Sentinel and use custom dashboards and artificial intelligence to rapidly uncover potential security incidents. Palo Alto Networks customers can also extend AutoFocus and other third-party threat intelligence to Azure Sentinel via our new integration between MineMeld and the Microsoft Graph Security API.”
Analyze and detect threats quickly with AI on your side – Security analysts face a huge burden from triaging as they sift through a sea of alerts, and correlate alerts from different products manually or using a traditional correlation engine. That’s why Azure Sentinel uses state of the art, scalable machine learning algorithms to correlate millions of low fidelity anomalies to present a few high fidelity security incidents to the analyst. ML technologies will help you quickly get value from large amounts of security data you are ingesting and connect the dots for you. For example, you can quickly see a compromised account that was used to deploy ransomware in a cloud application. This helps reduce noise drastically, in fact we have seen an overall reduction of up to 90 percent in alert fatigue during evaluations. Early adopters are seeing the benefits of threat detections with AI. Reed M. Wiedower, CTO of New Signature said, “We see a huge value with Azure Sentinel because of its ability to generate insights across a vast array of different pieces of infrastructure.”
These built-in machine learning models are based on the learnings from the Microsoft security team over many years of defending our customer’s cloud assets. You do not need to be a data scientist to leverage use these benefits you just turn them on. Of course, if you are a data scientist and you want to customize and enrich the detections then you can bring your own models to Azure Sentinel using the built-in Azure Machine Learning service. Additionally, Azure Sentinel can connect to user activity and behavior data from Microsoft 365 security products which can be combined with other sources to provide visibility into an entire attack sequence.
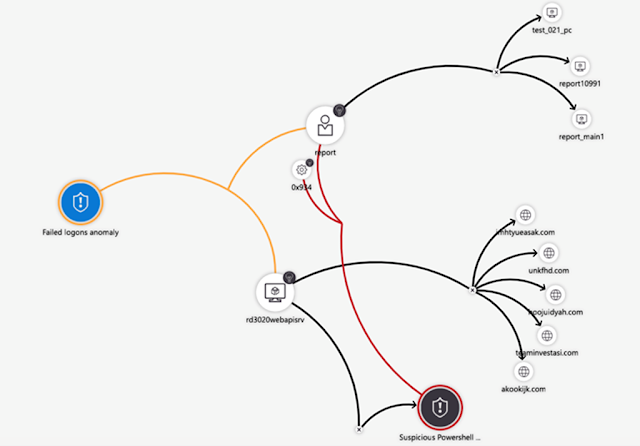
Investigate and hunt for suspicious activities – Graphical and AI-based investigation will reduce the time it takes to understand the full scope of an attack and its impact. You can visualize the attack and take quick actions in the same dashboard.
Proactive hunting of suspicious activities is another critical task for the security analysts. Often the process by which SecOps collect and analyze the data is a repeatable process which can be automated. Today, Azure Sentinel provides two capabilities that enable you to automate your analysis by building hunting queries and Azure Notebooks that are based on Jupyter notebooks. We have developed a set of queries and Azure Notebooks based on the proactive hunting that Microsoft’s Incident Response and Threat Analysts teams perform. As the threat landscape evolves, so will our queries and Azure Notebooks. We will provide new queries and Azure Notebooks via the Azure Sentinel GitHub community.
Automate common tasks and threat response – While AI sharpens your focus on finding problems, once you have solved the problem you don’t want to keep finding the same problems over and over – rather you want to automate response to these issues. Azure Sentinel provides built-in automation and orchestration with pre-defined or custom playbooks to solve repetitive tasks and to respond to threats quickly. Azure Sentinel will augment existing enterprise defense and investigation tools, including best-of-breed security products, homegrown tools, and other systems like HR management applications and workflow management systems like ServiceNow.
Microsoft’s unparalleled threat intelligence that is informed by analyzing 6.5+ trillions of signals daily and decades of security expertise at cloud scale will help you modernize your security operations.
“Azure Sentinel provides a proactive and responsive cloud-native SIEM that will help customers simplify their security operations and scale as they grow.”
Security doesn’t have to be an endless saga. Instead, put the cloud and large-scale intelligence to work. Make your threat protection smarter and faster with artificial intelligence. Import Microsoft Office 365 data for security analytics for free.





0 comments:
Post a Comment