We are pleased to announce several new Azure Firewall features that allow your organization to improve security, have more customization, and manage rules more easily. These new capabilities were added based on your top feedback:
◉ Custom DNS support now in preview.
◉ DNS Proxy support now in preview.
◉ FQDN filtering in network rules now in preview.
◉ IP Groups now generally available.
◉ AKS FQDN tag now generally available.
◉ Azure Firewall is now HIPAA compliant.
Azure Firewall is a cloud-native firewall as a service (FWaaS) offering that allows you to centrally govern and log all your traffic flows using a DevOps approach. The service supports both application and network-level filtering rules and is integrated with the Microsoft Threat Intelligence feed for filtering known malicious IP addresses and domains. Azure Firewall is highly available with built-in auto scaling.
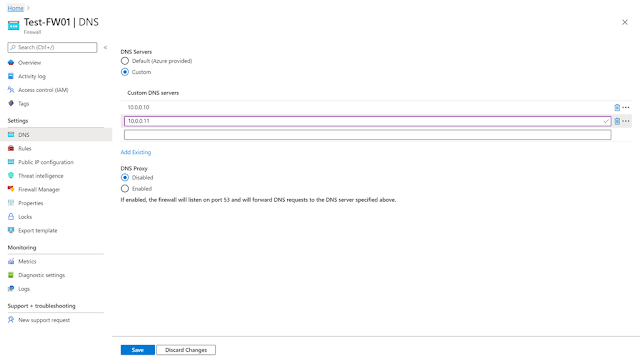
Since its launch in September 2018, Azure Firewall has been hardcoded to use Azure DNS to ensure the service can reliably resolve its outbound dependencies. Custom DNS provides separation between customer and service name resolution. This allows you to configure Azure Firewall to use your own DNS server and ensures the firewall outbound dependencies are still resolved with Azure DNS. You may configure a single DNS server or multiple servers in Azure Firewall and Firewall Policy DNS settings.
Azure Firewall is also capable of name resolution using Azure Private DNS, as long as your private DNS zone is linked to the firewall virtual network.
With DNS proxy enabled, outbound DNS queries are processed by Azure Firewall, which initiates a new DNS resolution query to your custom DNS server or Azure DNS. This is crucial to have reliable FQDN filtering in network rules. You may configure DNS proxy in Azure Firewall and Firewall Policy DNS settings.
DNS proxy configuration requires three steps:
1. Enable DNS proxy in Azure Firewall DNS settings.
2. Optionally configure your custom DNS server or use the provided default.
3. Finally, you must configure the Azure Firewall’s private IP address as a Custom DNS server in your virtual network DNS server settings. This ensures DNS traffic is directed to Azure Firewall.
◉ Custom DNS support now in preview.
◉ DNS Proxy support now in preview.
◉ FQDN filtering in network rules now in preview.
◉ IP Groups now generally available.
◉ AKS FQDN tag now generally available.
◉ Azure Firewall is now HIPAA compliant.
Azure Firewall is a cloud-native firewall as a service (FWaaS) offering that allows you to centrally govern and log all your traffic flows using a DevOps approach. The service supports both application and network-level filtering rules and is integrated with the Microsoft Threat Intelligence feed for filtering known malicious IP addresses and domains. Azure Firewall is highly available with built-in auto scaling.
Custom DNS support now in preview
Since its launch in September 2018, Azure Firewall has been hardcoded to use Azure DNS to ensure the service can reliably resolve its outbound dependencies. Custom DNS provides separation between customer and service name resolution. This allows you to configure Azure Firewall to use your own DNS server and ensures the firewall outbound dependencies are still resolved with Azure DNS. You may configure a single DNS server or multiple servers in Azure Firewall and Firewall Policy DNS settings.
Azure Firewall is also capable of name resolution using Azure Private DNS, as long as your private DNS zone is linked to the firewall virtual network.
DNS Proxy now in preview
With DNS proxy enabled, outbound DNS queries are processed by Azure Firewall, which initiates a new DNS resolution query to your custom DNS server or Azure DNS. This is crucial to have reliable FQDN filtering in network rules. You may configure DNS proxy in Azure Firewall and Firewall Policy DNS settings.
DNS proxy configuration requires three steps:
1. Enable DNS proxy in Azure Firewall DNS settings.
2. Optionally configure your custom DNS server or use the provided default.
3. Finally, you must configure the Azure Firewall’s private IP address as a Custom DNS server in your virtual network DNS server settings. This ensures DNS traffic is directed to Azure Firewall.
Figure 1. Custom DNS and DNS Proxy settings on Azure Firewall.
FQDN filtering in network rules now in preview
You can now use fully qualified domain names (FQDN) in network rules based on DNS resolution in Azure Firewall and Firewall Policy. The specified FQDNs in your rule collections are translated to IP addresses based on your firewall DNS settings. This capability allows you to filter outbound traffic using FQDNs with any TCP/UDP protocol (including NTP, SSH, RDP, and more). As this capability is based on DNS resolution, it is highly recommended you enable the DNS proxy to ensure your protected virtual machines and firewall name resolution are consistent.
FQDN filtering in application rules for HTTP/S and MSSQL is based on application level transparent proxy. As such, it can discern between two FQDNs that are resolved to the same IP address. This is not the case with FQDN filtering in network rules, so it is always recommended you use application rules when possible.
Figure 2. FQDN filtering in network rules.
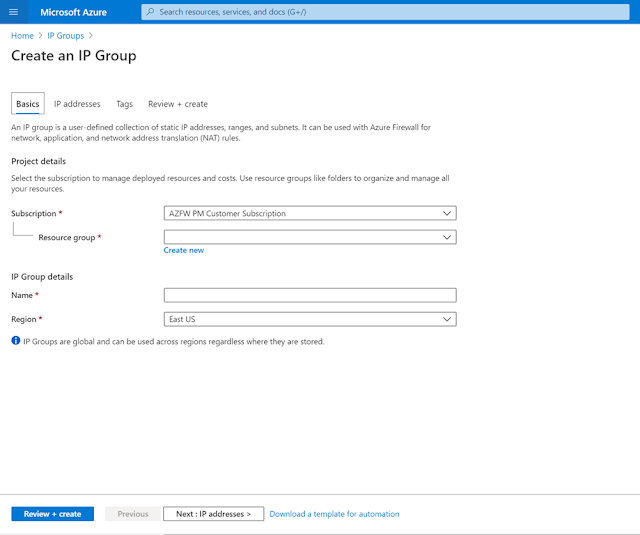
IP Groups now generally available
IP Groups is a new top-level Azure resource that allows you to group and manage IP addresses in Azure Firewall rules. You can give your IP group a name and create one by entering IP addresses or uploading a file. IP Groups eases your management experience and reduce time spent managing IP addresses by using them in a single firewall or across multiple firewalls. IP Groups is now generally available and supported within a standalone Azure Firewall configuration or as part of Azure Firewall Policy.
Figure 3. Creating a new IP Group.
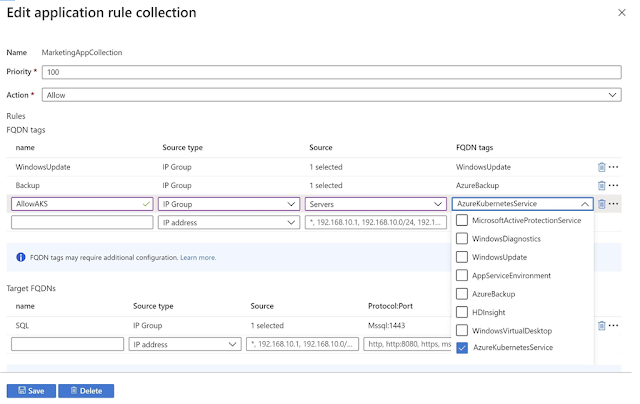
AKS FQDN tag now in generally available
An Azure Kubernetes Service (AKS) FQDN tag can now be used in Azure Firewall application rules to simplify your firewall configuration for AKS protection. Azure Kubernetes Service (AKS) offers managed Kubernetes cluster on Azure that reduces the complexity and operational overhead of managing Kubernetes by offloading much of that responsibility to Azure.
For management and operational purposes, nodes in an AKS cluster need to access certain ports and FQDNs. For more guidance on how to add protection for Azure Kubernetes cluster using Azure Firewall, see Use Azure Firewall to protect Azure Kubernetes Service (AKS) Deployments.
Figure 4. Configuring application rule with AKS FQDN tag.
Source: azure.microsoft.com




0 comments:
Post a Comment