We continue to be amazed by the adoption, interest, positive feedback, and the breadth of use cases customers are finding for our service. Today, we are happy to share several key Azure Firewall capabilities as well as an update on recent important releases into general availability and preview.
◉ Intrusion Detection and Prevention System (IDPS) signatures lookup now generally available.
◉ TLS inspection (TLSi) Certification Auto-Generation now generally available.
◉ Web categories lookup now generally available.
◉ Structured Firewall Logs now in preview.
◉ IDPS Private IP ranges now in preview.
Azure Firewall is a cloud-native firewall-as-a-service offering that enables customers to centrally govern and log all their traffic flows using a DevOps approach. The service supports both application and network-level filtering rules and is integrated with the Microsoft Threat Intelligence feed for filtering known malicious IP addresses and domains. Azure Firewall is highly available with built-in auto-scaling.
IDPS signatures lookup
Azure Firewall Premium IDPS signature lookup is a great way to better understand the applied IDPS signatures on your network as well as fine-tuning them according to your specific needs. IDPS signatures lookup allows you to:
◉ Customize one or more signatures and change their mode to Disabled, Alert, or Alert and Deny. For example, if you receive a false positive where a legitimate request is blocked by Azure Firewall due to a faulty signature, you can use the signature ID from the network rules logs and set its IDPS mode to off. This causes the "faulty" signature to be ignored and resolves the false positive issue.
◉ You can apply the same fine-tuning procedure for signatures that are creating too many low-priority alerts, and therefore interfering with visibility for high-priority alerts.
◉ Get a holistic view of the entire 58,000 signatures.
◉ Smart search.
◉ Allows you to search through the entire signatures database by any type of attribute. For example, you can search for specific CVE-ID to discover what signatures are taking care of this CVE by typing the ID in the search bar.
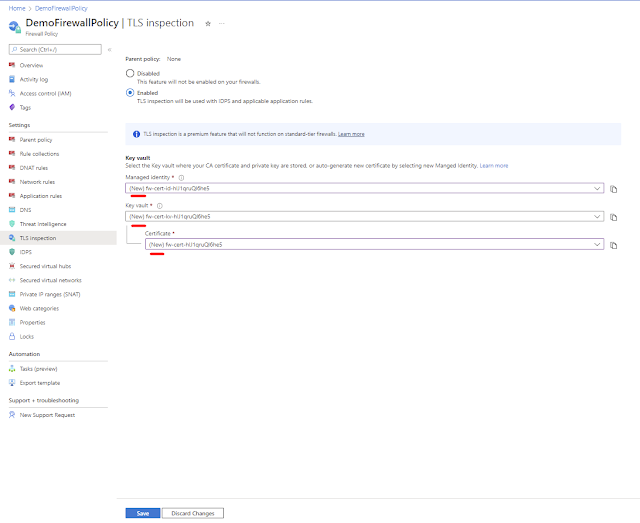
TLSi Certification Auto-Generation
For non-production deployments, you can use the Azure Firewall Premium TLS inspection Certification Auto-Generation mechanism, which automatically creates the following three resources for you:
◉ Managed Identity
◉ Key Vault
◉ Self-signed Root CA certificate
Just choose the new managed identity, and it ties the three resources together in your Premium policy and sets up TLS inspection.
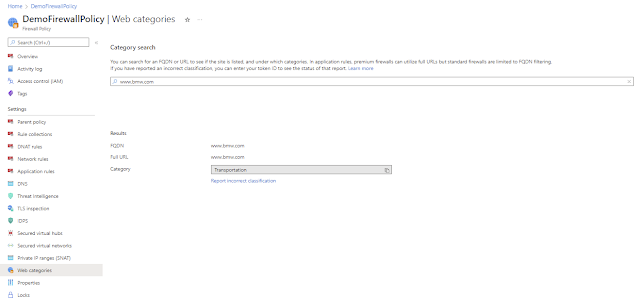
Web categories lookup
Web Categories is a filtering feature that allows administrators to allow or deny web traffic based on categories, such as gambling, social media, and more. We added tools that help manage these web categories: Category Check and Mis-Categorization Request.
Using Category Check, an admin can determine which category a given FQDN or URL falls under. In the case that a FQDN or URL fits better under a different category, an administrator can also report an incorrect classification, in which the request will be evaluated and updated if approved.
Structured Firewall Logs
Today, the following diagnostic log categories are available for Azure Firewall:
◉ Application rule log
◉ Network rule log
◉ DNS proxy log
With this new feature, customers will be able to choose using
Resource Specific Tables instead of the existing
AzureDiagnostics table. In case both sets of logs are required, at least two diagnostic settings would need to be created per firewall.
In Resource Specific mode, individual tables in the selected workspace are created for each category selected in the diagnostic setting.
This method is recommended since it makes it much easier to work with the data in log queries, provides better discoverability of schemas and their structure, improves performance across both ingestion latency and query times, and the ability to grant Azure role-based access control (RBAC) rights on a specific table.
New Resource Specific tables are now available in diagnostic setting allowing users to utilize the following newly added categories:
◉
Network rule log: contains all Network Rule log data. Each match between data plane and network rule creates a log entry with the data plane packet and the matched rule's attributes.
◉
NAT rule log: contains all destination network address translation (DNAT) events log data. Each match between data plane and DNAT rule creates a log entry with the data plane packet and the matched rule's attributes.
◉
Application rule log: contains all Application rule log data. Each match between data plane and Application rule creates a log entry with the data plane packet and the matched rule's attributes.
◉
IDPS log: contains all data plane packets that were matched with one or more IDPS signatures.
Additional Kusto Query Language (KQL) log queries were added (as seen in the diagram below) to query structured firewall logs.

IDPS Private IP ranges
In Azure Firewall Premium IDPS, Private IP address ranges are used to identify if traffic is inbound or outbound. By default, only ranges defined by Internet Assigned Numbers Authority (IANA) RFC 1918 are considered private IP addresses. To modify your private IP addresses, you can now easily edit, remove or add ranges as needed.
Source: microsoft.com








0 comments:
Post a Comment