Microsoft Azure is constantly evolving to meet the needs of its growing user base. In response to the feedback and requirements of developers, we have announced a new SKU for Azure Bastion: Bastion Developer. This service, now in public preview, will be a game-changer for developers seeking secure, cost-effective, and hassle-free connectivity to their Azure Virtual Machines. In this blog post, we’ll explore what Azure Bastion Developer is, the problems this new SKU addresses, and why it’s a must-try solution for developers.
What is Azure Bastion Developer?
Azure Bastion Developer is a new low-cost, zero-configuration, always-on SKU of the Azure Bastion service. Its primary mission is to provide secure-by-default Remote Desktop Protocol (RDP) and Secure Shell (SSH) access to Azure Virtual Machines, allowing users to establish secure connections to a single Virtual Machine at a time without the need for additional network configurations or public IP addresses on Virtual Machines. This service is designed to simplify and enhance the process of accessing your Azure Virtual Machines by eliminating the complexities, high costs, and security concerns often associated with alternative methods.
Addressing developer pain points
Azure Bastion Developer has been developed with the aim of addressing three common issues that developers encounter when connecting to Azure Virtual Machines:
1. Discovery
When developers create standalone Virtual Machines, they may not actively seek out Azure Bastion, and it might not be readily apparent during the Virtual Machine creation process. While IT professionals are familiar with the concept of a bastion host or jump-box server, the average Azure user may not be. This could lead to the use of less secure public IP-based access methods. Azure Bastion Developer solves this problem by providing secure and seamless access directly in the Virtual Machine blade. In the coming months, Bastion Developer will populate as the recommended connectivity option in the Virtual Machine connect experience for available regions.
2. Usability
Setting up Azure Bastion has traditionally required users to deploy a new resource and follow a series of configuration steps, including the creation of a dedicated subnet. While these steps might be manageable for technically savvy users, they can be complex and time-consuming for many. Azure Bastion Developer simplifies the process by offering an easy-to-use, zero-configuration solution. Users can opt-in to use it during Virtual Machine connection, making secure access a breeze.
3. Cost
Azure Bastion Basic, while a powerful tool, may be a potentially expensive choice for developers who spend a few hundred dollars or less in Azure each month, leading them to connect with less secure public IP based options. Azure Bastion Developer addresses this concern by providing an option that comes at a more affordable price point than public IP. This cost-effective pricing will make Azure Bastion Developer the default private connectivity option in Azure, enabling developers to enjoy secure access without breaking the bank. The public preview of Bastion Developer will be free with more details on pricing when generally available.
Connectivity Options with Azure Bastion Developer
1. Portal-based access (public preview). Bastion Developer will offer support for RDP connections for Windows Virtual Machines and SSH connections for Linux Virtual Machines in the Azure portal.
2. Native client-based access for SSH (roadmap). Bastion Developer will offer support for SSH connections for Linux Virtual Machines via Azure Command Line Interface (CLI) in the coming months.
Feature comparison of Azure Bastion offerings
Bastion Developer will be a lightweight SKU of the Bastion service, allowing a single connection per user directly through the Virtual Machines connect experience. Bastion Developer is ideal for Dev/Test users who want to securely connect to their Virtual Machines without the need for additional features or scaling. The feature matrix below outlines the differences between Bastion Developer and Bastion Basic and Standard SKUs.
| Features | Developer | Basic | Standard |
| Private connectivity to Virtual Machines | Yes | Yes | Yes |
| Dedicated host agent | No | Yes | Yes |
| Support for multiple connections per user | No | Yes | Yes |
| Linux Virtual Machine private key in AKV | No | Yes | Yes |
| Support for Network Security Groups | No | Yes | Yes |
| Audit logging | No | Yes | Yes |
| Kerberos support | No | Yes | Yes |
| VNET peering support | No | Yes | Yes |
| Host scaling (2-50 instances) | No | No | Yes |
| Custom port and protocol | No | No | Yes |
| Native SSH support via Azure CLI | Roadmap | Roadmap | Yes |
| Native RDP support via Azure CLI | No | No | Yes |
| Azure Active Directory login for RDP/SSH via native client | No | No | Yes |
| IP-based connection | No | No | Yes |
| Shareable links | No | No | Yes |
How to get started
We invite you to preview Azure Bastion Developer in your cloud environment.
1. Navigate to the Azure portal.
2. Deploy a Windows or Linux Virtual Machine in one of the regions below. Note that Bastion Developer is currently only available in the following regions:
- Central United States EUAP
- East United States 2 EUAP
- West Central United States
- North Central United States
- West United States
- North Europe
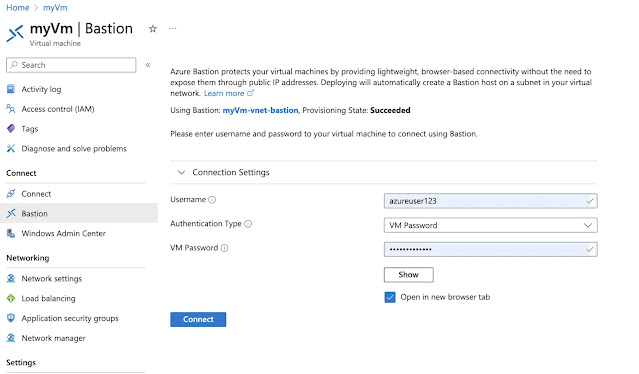
3. Navigate to the Bastion tab in the Virtual Machine blade and click Deploy Bastion Developer. (Bastion Basic and Standard deployments will be moved under “Dedicated Deployment Options”).
4. Once your Bastion Developer resource is deployed, enter your Virtual Machine username and password and select Connect to securely connect to your Virtual Machine in the browser.





0 comments:
Post a Comment