As the holiday season of 2023 unfolded, it brought not only cheer and celebration but also a surge in Distributed Denial-of-Service (DDoS) attacks. This year’s trends in DDoS attacks reveal a complex and evolving threat landscape. From misconfigured Docker API endpoints enabling botnet delivery to the emergence of NKAbuse malware exploiting blockchain technology for DDoS attacks, the tactics and scale of these attacks have shown significant sophistication and diversification.
The 2023 holiday season attack landscape in Azure
In our monitoring of the attack landscape during the holiday season, we observed a notable shift in some of the attack patterns compared to the previous year. This change underscores the relentless efforts of malicious actors to refine their threat tactics and attempt to circumvent DDoS protection strategies.
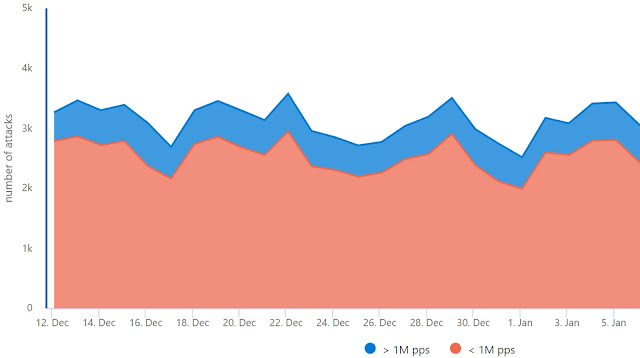
Daily Attack Volume: Azure’s robust security infrastructure automatically mitigated a peak of 3,500 attacks daily. Notably, large-scale attacks, exceeding 1 million packets per second (pps), constituted 15%-20% of these incidents.*
Figure 1: Number of daily DDoS attacks towards resources in Azure.
Geographical origins: A shift in attack origins was observed, with the top two origin countries being China with 42% of the attacks and the USA with 18%. All other countries make up 40% of attacks.* This marks a change from the previous year, where both countries were equally represented as the top two regional sources.
Figure 2: Source countries for DDoS Attacks on Azure.
Attack protocols: The 2023 holiday season saw a predominant use of UDP-based attacks, targeting gaming workloads and web applications, accounting for 78% of the attacks. These include UDP reflected/amplified attacks, which predominantly leverage domain name system (DNS) and simple service discovery protocol (SSDP), as well as quick UDP internet connections (QUIC) for reflection purposes. Notably, QUIC is emerging as a more common attack vector, either by reflection or by DDoS stressors that utilize UDP port 443 randomly. This year’s holiday season attack patterns contrast sharply with the previous year, where TCP-based attacks dominated 65% of all attacks.*
Figure 3: Attacks protocols distribution.
Record-breaking attack: A staggering UDP attack, peaking at 1.5 terabits per second (Tbps), targeted a gaming customer in Asia. This attack, originating from China, Japan, the USA, and Brazil, was highly randomized, involving numerous source IPs and ports, yet was fully mitigated by Azure’s defenses.
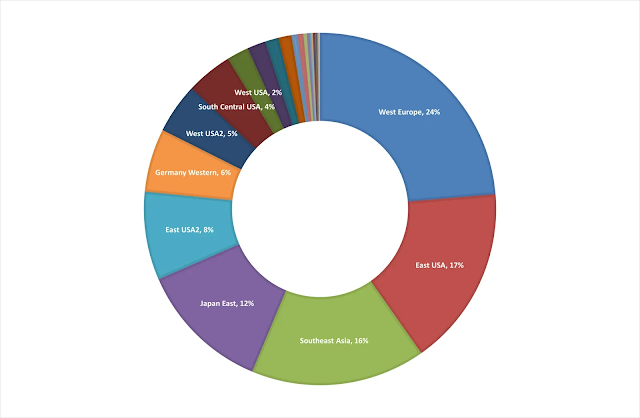
Botnet evolution: In the past year, cybercriminals increasingly leveraged cloud resources, particularly virtual machines, for DDoS attacks. This trend continued to evolve during the holiday season, with attackers trying to exploit discounted Azure subscriptions globally. From mid-November 2023 and until end of year, we monitored compromised account attempts in 39 Azure regions, with Europe and the USA being the primary targets, accounting for about 67% of these incidents.* Azure’s defense mechanisms successfully neutralized these threats.
Figure 4: Azure regions where attempts to exploit resources for DDOS attacks occurred.
Contextualizing the threat
The 2023 DDoS attack trends in Azure mirror global patterns. Attacks are becoming politically motivated as we highlighted earlier last year, fueled by geopolitical tensions.
The emergence of DDoS-for-hire services, commonly known as “stressers” and “booters” remain popular amongst attackers. These platforms, readily available on cybercriminal forums, have democratized the ability to launch powerful DDoS attacks, making them accessible to less sophisticated criminals for minimal costs. Recent years have seen an uptick in the availability and use of these services, confirmed by international law enforcement agencies through operations like Operation PowerOFF, which last year in May targeted 13 domains associated with DDoS-for-hire platforms. Despite these efforts, stressers continue to thrive, offering a range of attack methods and power, with some capable of attacks up to 1.5 Tbps.
Cloud power: Combating the evolving DDoS threats
The rise of botnets at scale and DDoS-for-hire services poses a significant risk to online services and business operations. To fight these threats, more cloud computing power is needed to absorb the leading wave of the attack until patterns can be identified, spurious traffic diverted, and legitimate traffic preserved. When tens of thousands of devices constitute an attack, the cloud is our best defense, due to the scale needed to mitigate the largest attacks. In addition, due to the global distribution of the cloud, closer proximity helps to block attacks closest to the sources.
Ensuring robust protection
In an era where digital threats are constantly evolving, ensuring robust protection against DDoS attacks has never been more critical. Here’s how Azure’s comprehensive security solutions are designed to safeguard your digital infrastructure.
DDoS Protection Service: With the high risk of DDoS attacks, it’s essential to have a DDoS protection service like Azure DDoS Protection. This service provides always-on traffic monitoring, automatic attack mitigation upon detection, adaptive real-time tuning, and full visibility on DDoS attacks with real-time telemetry, monitoring, and alerts.
Multi-Layered Defense: For comprehensive protection, set up a multi-layered defense by deploying Azure DDoS Protection with Azure Web Application Firewall (WAF). Azure DDoS Protection secures the network layer (Layer 3 and 4), while Azure WAF safeguards the application layer (Layer 7). This combination provides protection against various types of DDoS attacks.
Alert Configuration: Azure DDoS Protection can identify and mitigate attacks without user intervention. Configuring alerts for active mitigations can keep you informed about the status of protected public IP resources.
2024: Rising against DDoS threats
The 2023 holiday season has underscored the relentless and evolving threat of DDoS attacks in the cyber landscape. As we transition into the new year, it becomes crucial for organizations to enhance and adapt their cybersecurity strategies. This period should be a learning curve, focusing on fortifying defenses against such DDoS attacks and staying vigilant against new tactics. The resilience of Azure against these sophisticated DDoS threats highlights the critical need for robust and adaptive security measures, not just in protecting digital assets but also in ensuring uninterrupted business operations.
* Based on internal data
Source: microsoft.com








0 comments:
Post a Comment